Hieu Nguyen
April 16, 2025
•
15 mins read

Integrating source control between Retool and GitHub enables robust version management for applications, queries, workflows, and collaborative development. This guide provides a detailed walkthrough of the configuration process, addressing common pitfalls and clarifying technical requirements. By following these steps, teams can implement a secure, audit-friendly workflow with branch protection, pull request reviews, and automated deployments. Integrating Retool source control with GitHub ensures smooth versioning, deployment, and teamwork.
Begin by initializing a new repository in GitHub with strict isolation from existing projects. Navigate to Your Profile > Repositories > New and configure:
Retool’s source control integration requires a mainbranch as the canonical source of truth. Setting up a dedicated Retool GitHub App allows secure and scalable API access for your applications. Avoid modifying this branch directly-all changes must flow through protected branches and pull requests.
GitHub Apps provide granular permissions compared to personal access tokens. Create one via GitHub Settings > Developer Settings > GitHub Apps > New GitHub App with these critical settings:

After creation, install the app on the target repository and note two identifiers:
https://github.com/settings/installations/[ID]).From the GitHub App’s Private Keys section, generate a PEM-formatted key. This key must be:
# Linux/macOS
base64 -w 0 private-key.pem > encoded-key.txt
# PowerShell
$keyBytes = [System.IO.File]::ReadAllBytes("[private-key].pem")
[System.Convert]::ToBase64String($keyBytes) | Out-File "[encoded-key].txt"openssl dgst -sha256 -binary [private-key].pem | base64Mismatches indicate file corruption or encoding errors-regenerate the key if discrepancies occur.
For self-hosted Retool instances behind corporate firewalls, allowlist GitHub’s IP ranges (140.82.112.0/20, 192.30.252.0/22) and Retool’s outbound IPs based on region:

Cloud-hosted Retool organizations must enable Allow access from Retool IPS in GitHub repository settings and have an Enterprise plan.
In Retool’s Settings > Source Control > GitHub, provide:
encoded-key.txt.owner/repo-name.Click Test Connection to validate credentials and network connectivity. Common failures include:
Connecting Retool to GitHub properly is critical to avoid sync issues and ensure your Retool GitHub integration works smoothly across environments.
In Retool’s editor, Protect an app to create a feature branch. This:
main branch against direct edits.Retool allows atomic commits spanning apps, queries, JavaScript modules, and workflows.
When committing:
feat: Add OAuth2 login workflow).After PR approval:
If Retool’s deployment fails due to repository drift:
git fetch origin && git reset --hard origin/main in Retool instance’s console.Require signed commits and Require status checks to enforce code reviews.
Extend Retool’s native deployment with GitHub Actions. Adding CI/CD pipelines to your Retool GitHub integration speeds up testing, ensures consistency, and cuts down human errors during production deployments:
name: Retool Deployment Check
on:
workflow_run:
workflows: ["Deploy Production"]
types:
- completed
jobs:
post-deploy:
runs-on: ubuntu-latest
steps:
- name: Verify Retool Deployment
run: |
curl -X POST -H "Authorization: Bearer $RETOOL_API_KEY" \
https://$RETOOL_INSTANCE/api/deployments/$DEPLOYMENT_ID/verifyIntegrating Retool with GitHub source control establishes an enterprise-grade framework for application lifecycle management. By adhering to the authentication protocols, network policies, and merge strategies outlined here, organizations can achieve audit compliance, reduce deployment errors, and streamline collaborative development. Future enhancements may include native support for GitOps workflows and granular permission modeling within Retool’s interface.
At Retoolers, we help businesses create custom dashboards, admin panels, client portals, and full workflow automation solutions using Retool. From idea to execution, we’ve got the skills to make it happen.
Let’s build something great together — contact Retoolers today.
Looking to supercharge your operations? We’re masters in Retool and experts at building internal tools, dashboards, admin panels, and portals that scale with your business. Let’s turn your ideas into powerful tools that drive real impact.
Curious how we’ve done it for others? Explore our Use Cases to see real-world examples, or check out Our Work to discover how we’ve helped teams like yours streamline operations and unlock growth.
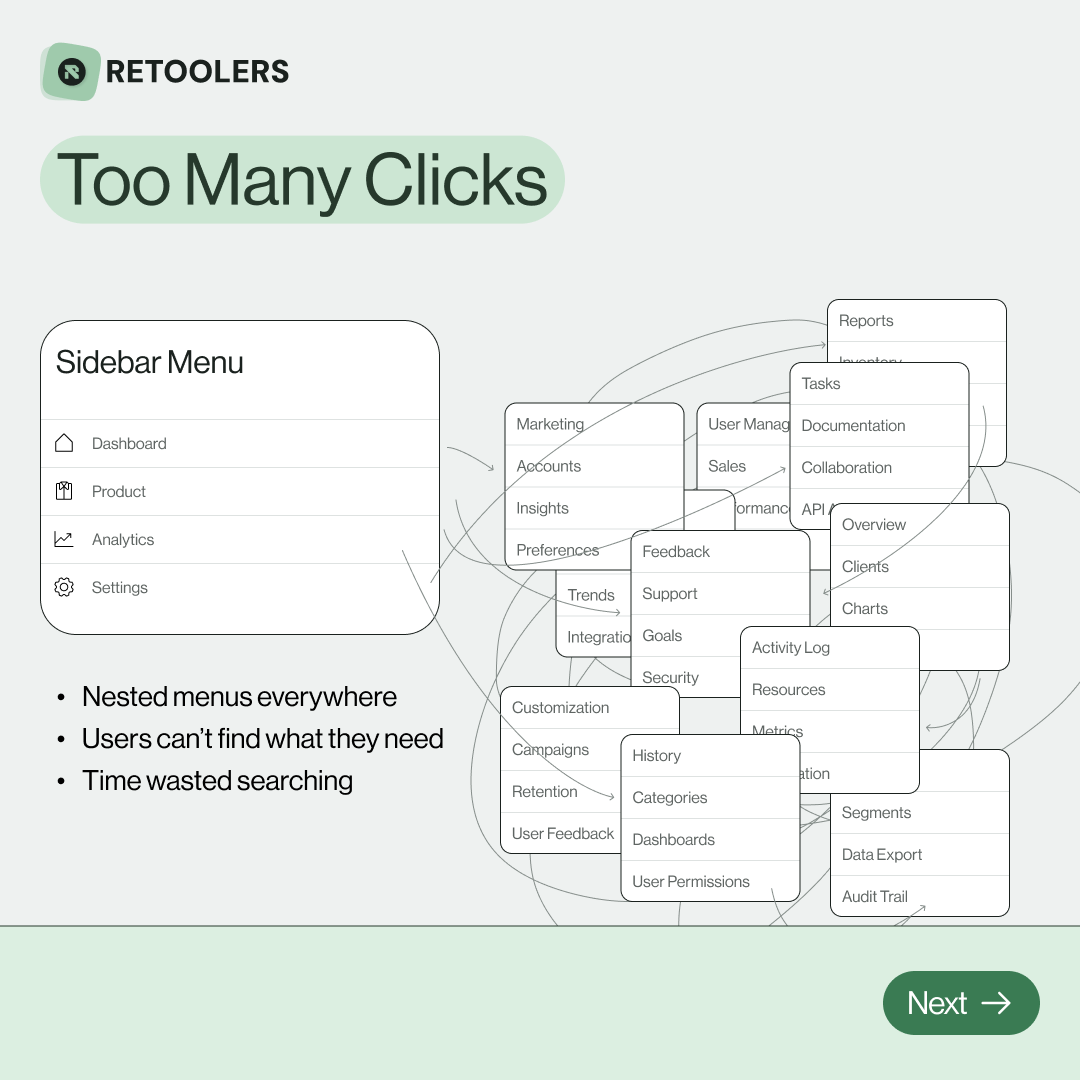
🔎 Internal tools often fail because of one simple thing: Navigation.
Too many clicks, buried menus, lost users.
We broke it down in this 4-slide carousel:
1️⃣ The problem (too many clicks)
2️⃣ The fix (clear navigation structure)
3️⃣ The Retool advantage (drag-and-drop layouts)
4️⃣ The impact (happier teams)
💡 With Retool, you can design internal tools that are easy to use, fast to build, and simple to maintain.
👉 Swipe through the carousel and see how better UX = better productivity.
📞 Ready to streamline your tools? Book a call with us at Retoolers.

🚀From idea → app in minutesBuilding internal tools used to take weeks.
Now, with AI App Generation in Retool, you can describe what you want in plain English and let AI do the heavy lifting.
At Retoolers, we help teams move faster by combining AI + Retool to create tools that actually fit their workflows.
👉 Check out our blog for the full breakdown: https://lnkd.in/gMAiqy9F
As part of our process, you’ll receive a FREE business analysis to assess your needs, followed by a FREE wireframe to visualize the solution. After that, we’ll provide you with the most accurate pricing and the best solution tailored to your business. Stay tuned—we’ll be in touch shortly!